 The
University of Adelaide
Home |
School EEE
The
University of Adelaide
Home |
School EEE 

ELEC ENG 4039A/B
FINAL YEAR HONOUR PROJECT
OPTIMISATION WLAN FOR BROADBAND ACCESS

Related Link
Dynamic Changing Fragmentation Threshold
In wireless technologies, the physical medium that the data is passed over is, instead of an Ethernet wired cable, in the form of electromagnetic waves. Data however is still passed across this medium in a similar fashion to the wired network, in a frame, see Figure 3.1.
This frame contains all the data for processing the internal payload, such as information for addressing and error checking. It is not the internal data of the frame here that is of interest, but rather how it is transmitted across the medium. When the data is transmitted, each frame can be split into parts to be sent. This is known as fragmentation and in wireless LAN, where the probability of interference is high, fragmentation is a good way of increasing the reliability of the link [12]. The fragmentation threshold specifies the maximum size packet 17 that can be sent across the link, which is normally set to between 256 and 2048 bytes [30].
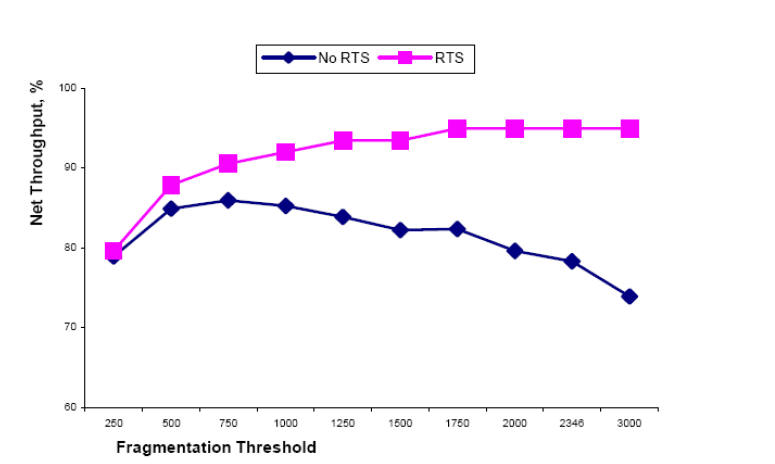
Figure 1- Fragmentation Threshold [31]
The technique works well under bad link conditions, such as when there is noise on the link. When a packet is lost, the wireless protocol acts to resend the packet, by limiting the size of these packets, that is by lowering the threshold it is highly probable that only some of the information will be lost and need resending. Thus not as much data needs to be retransmitted unnecessarily, increasing the reliability of the link. If however the link is under good conditions, the extra overhead needed for fragmentation can slow data transmission, thus the fragmentation threshold would need to be increased.
A study by Sweet and Sidhu [31] investigates the performance of the IEEE 802.11 wireless LAN and shows this relationship between fragmentation threshold and throughput. Figure 1, taken from this paper, shows that there is a point at which the throughput will be optimised for a particular fragmentation threshold. If the fragmentation is too high the throughput is not at its maximum, as when a packet is lost the whole packet needs retransmission, too low and the amount of overhead decreases the throughput. It is here that it is suggested that by producing code that dynamically changes the fragmentation threshold in the wireless LAN it will provide better reliability and higher throughput under changing conditions. From the suggested arguments on fragmentation, optimisation 18 should occur when the link quality reaches a poor enough value for the fragmentation to make a positive difference.
Hill Climbing Method
The optimisation techniques were revisited and research was made into different methods such as using genetic algorithms, which adapt to the environments. It was found that most algorithms require too much memory and the Hill Climbing Method, in its simplicity, is most suited for this optimisation process.
Hill Climbing optimisation is a greedy method; in that it always searches for the maximum, taking steps in the direction that improves the state of the system. If the step is in the wrong direction, two steps are taken in the other direction to counteract this on the next move. The algorithm was adapted for moving hills where the maximum value may change as the quality of the link increases or decreases. Only needing to know the previous link quality and the current link quality the fragmentation threshold that maximizes throughput can be efficiently calculated with small memory usage.
The algorithm is run when there is a great enough drop in link quality to ensure it is not just small fluctuations. To improve the speed of finding the maximum value the size of the steps can be changed depending on how close to the maximum it is believed to be, these factors were not optimised due to time constraints but would be possible improvements in the future.
Algorithm
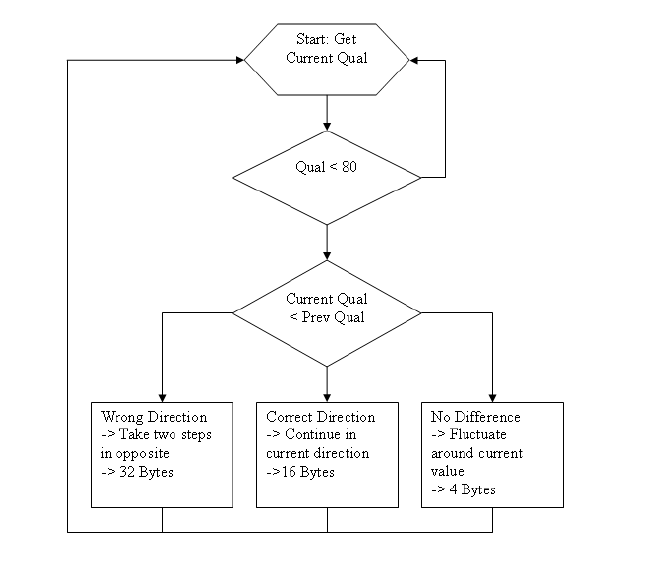
Figure 2 - Dynamic Changing Fragmentation Threshold Algorithm
Details of Optimisation Techniques:
Dynamic Changing Fragmentation Threshold
Back HOME
Copyright © The University of Adelaide 2006
Copyright | Disclaimer | Privacy
